포트 미러링
위키백과, 우리 모두의 백과사전.
포트 미러링(Port Mirroring)은 네트워크 스위치의 어떤 한 포트에서 보이는 모든 네트워크 패킷 혹은 전체 VLAN의 모든 패킷들을 다른 모니터링 포트로 복제하는데 사용된다. 포트 미러링은 주로 침입 탐지 시스템이나 패시브 프로브 또는 애플리케이션 성능 관리(Application Performance Management, APM)에 필요한 실사용자 모니터링(Real User Monitoring, RUM) 기술과 같이 네트워크 트래픽을 모니터링 해야하는 네트워크 장비들에서 사용된다. 포트미러링은 시스코 스위치에선 일반적으로 스위치 포트 분석기(Switched Port ANalyzer, SPAN) 혹은 원격 스위치 포트 분석기(Remote Switched Port ANalyzer, RSPAN)라 불린다. 다른 제조사들에서는 다른 이름으로 부르곤 하는데, 3Com의 경우 로빙 분석 포트(Roving Analysis Port, RAP)라 부른다.
네트워크 엔지니어/관리자는 포트 미러링을 네트워크상의 데이터를 분석 및 디버그하거나 오류를 진단하는데 사용한다. 포트 미러링은 또한 관리자가 네트워크 성능을 관찰하는데 도움을 주고, 문제가 발생했을 때 이를 알려준다. 또한 인바운드나 아웃바운드 트래픽 중 하나 혹은 전부를 하나 또는 여러개의 인터페이스로 미러링하는데 사용할 수 있다.
1. CISCO 포트 미러링(SPAN) 명령어
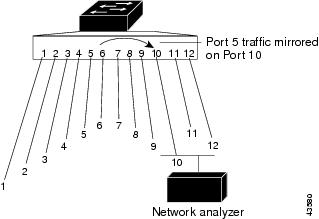
- 포트 gi0/5번 in, out 패킷을 gi0/10번으로 미러링
Switch#config terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#monitor session 1 source interface GigabitEthernet 0/5
Switch(config)#monitor session 1 destination interface GigabitEthernet 0/10
- 포트 gi0/5번 in 패킷을 gi0/10번으로 미러링
Switch#config terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#monitor session 1 source interface GigabitEthernet 0/5 rx
Switch(config)#monitor session 1 destination interface GigabitEthernet 0/10
- 포트 gi0/5번 out 패킷을 gi0/10번으로 미러링
Switch#config terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#monitor session 1 source interface GigabitEthernet 0/5 tx
Switch(config)#monitor session 1 destination interface GigabitEthernet 0/10
[출처] 시스코스위칭에서의 포트미러링 방법|작성자 보물섬
참고자료 : CISCO 가이드----------------------------------
Creating a Local SPAN Session
Follow these steps to create a SPAN session and specify the source (monitored) ports or VLANs and the destination (monitoring) ports.
SUMMARY STEPS
1. enable
2. configure terminal
3. no monitor session {session_number | all | local | remote}
4. monitor session session_number source {interface interface-id | vlan vlan-id} [, | -] [both | rx | tx]
5. monitor session session_number destination {interface interface-id [, | -] [encapsulation replicate]}
6. end
7. show running-config
8. copy running-config startup-config
DETAILED STEPS
Command or ActionPurpose
| Step 1 | enable Example: |
Enables privileged EXEC mode. Enter your password if prompted.
|
| Step 2 | configure terminal Example: |
Enters the global configuration mode. |
| Step 3 | no monitor session {session_number | all | local | remote} Example: |
Removes any existing SPAN configuration for the session.
|
| Step 4 | monitor session session_number source {interface interface-id | vlan vlan-id} [, | -] [both | rx | tx] Example: |
Specifies the SPAN session and the source port (monitored port).
|
| Step 5 | monitor session session_number destination {interface interface-id [, | -] [encapsulation replicate]} Example: |
Specifies the SPAN session and the destination port (monitoring port).
(Optional) encapsulation replicate specifies that the destination interface replicates the source interface encapsulation method. If not selected, the default is to send packets in native form (untagged). |
| Step 6 | end Example: |
Returns to privileged EXEC mode. |
| Step 7 | show running-config Example: |
Verifies your entries. |
| Step 8 | copy running-config startup-config Example: |
(Optional) Saves your entries in the configuration file. |
Creating a Local SPAN Session and Configuring Incoming Traffic
Follow these steps to create a SPAN session, to specify the source ports or VLANs and the destination ports, and to enable incoming traffic on the destination port for a network security device (such as a Cisco IDS Sensor Appliance).
SUMMARY STEPS
1. enable
2. configure terminal
3. no monitor session {session_number | all | local | remote}
4. monitor session session_number source {interface interface-id | vlan vlan-id} [, | -] [both | rx | tx]
5. monitor session session_number destination {interface interface-id [, | -] [encapsulation replicate] [ingress {dot1q vlan vlan-id | untagged vlan vlan-id | vlan vlan-id}]}
6. end
7. show running-config
8. copy running-config startup-config
DETAILED STEPS
Command or ActionPurpose
| Step 1 | enable Example: |
Enables privileged EXEC mode. Enter your password if prompted.
|
| Step 2 | configure terminal Example: |
Enters the global configuration mode. |
| Step 3 | no monitor session {session_number | all | local | remote} Example: |
Removes any existing SPAN configuration for the session.
|
| Step 4 | monitor session session_number source {interface interface-id | vlan vlan-id} [, | -] [both | rx | tx] Example: |
Specifies the SPAN session and the source port (monitored port). |
| Step 5 | monitor session session_number destination {interface interface-id [, | -] [encapsulation replicate] [ingress {dot1q vlan vlan-id | untagged vlan vlan-id | vlan vlan-id}]} Example: |
Specifies the SPAN session, the destination port, the packet encapsulation, and the ingress VLAN and encapsulation.
|
| Step 6 | end Example: |
Returns to privileged EXEC mode. |
| Step 7 | show running-config Example: |
Verifies your entries. |
| Step 8 | copy running-config startup-config Example: |
'네트워크' 카테고리의 다른 글
| PPP(Point to Point Protocol) (0) | 2020.03.24 |
|---|---|
| OPENVPN MTU (0) | 2020.03.19 |
| OpenVPN Packet loss (0) | 2020.03.10 |
| /26 서브넷 주소 범위 (0) | 2020.01.02 |
| 네트워크 회선 속도 이슈 (0) | 2020.01.02 |